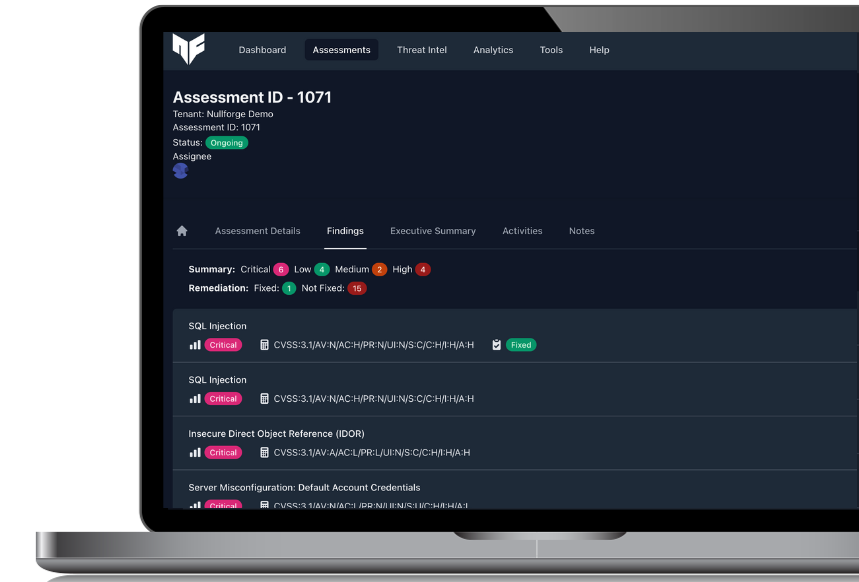
Real-time visibility. Confident decisions.
Nullforge Hive™ delivers continuous insight during vulnerability assessments and penetration tests. Track findings in real time, collaborate securely, and download reports the moment testing concludes.
-
Real-Time Visibility
See vulnerabilities as they’re found for earlier triage.
-
Reports On-the-Fly
Export polished PDFs immediately after testing.
-
Executive Summary
Leadership-ready impact, right in the portal.









